This module is a resource for lecturers
Exercises
This section contains material that is meant to support lecturers and provide ideas for interactive discussions and case-based analysis of the topic under consideration.
Exercise # 1 - Responsible Disclosure
Have students research how the largest technology companies such as Facebook, Google and Microsoft handle vulnerability reports. Ask them to answer the following:
- What mechanisms do they have to facilitate reporting process?
- What kind of rewards do they offer for the security researchers?
- Should responsible disclosure be protected under law? Why do you think so?
- Should security researchers get paid to disclose vulnerabilities?
Exercise # 2 - Situational Crime Prevention
Cornish and Clarke (2003) proposed five strategies and 25 techniques (with five techniques under each strategy) to prevent and reduce crime. Assign your students to choose a cybercrime and fill out the cybersecurity techniques they would use in the below table that could be used to prevent and/or reduce that cybercrime.
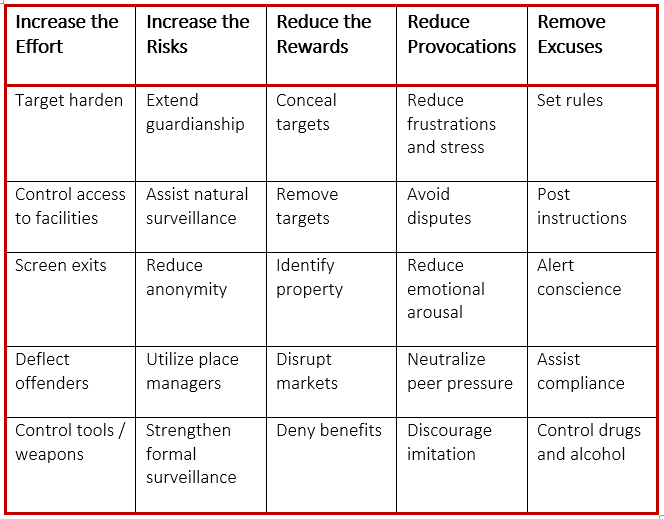
In addition, students should be prepared to answer the following question:
- Are there any techniques that do not apply to your chosen cybercrime? Please justify your response.
Exercise # 3 - Detection, Response, Recovery, and Preparedness
Instruct your students to conduct research in order to identify a cybersecurity incident that involved either a private organization or public agency within the last two years. Students should come prepared to discuss their selected cybersecurity incident and the answers to the below questions in class.
Discussion Questions
- How was the cybersecurity incident detected?
- In what ways did the organization or agency respond to the incident?
- What actions did the organization or agency take to recover from the incident?
- Was the organization or agency prepared for the incident? Why do you think so?
 Next:
Possible class structure
Next:
Possible class structure
 Back to top
Back to top