This module is a resource for lecturers
Risk
Decisions to safeguard assets are made under conditions of uncertainty; that is, they are made in the absence of absolute knowledge about potential threats, vulnerabilities, and exploitation of these vulnerabilities (Knight, 1921). Originally, risk was narrowly defined as the probability (or likelihood) of a threat and its impact (or consequences) should it materialize (Dali and Lajtha, 2012). This conception of risk is depicted in the following formula:
R
isk = P
robability x I
mpact
Formulas, such as the one depicted above, are used to quantify risks (for information on how to quantify cybersecurity risks and the limitations of these efforts, see: Freund and Jones, 2015; Hubbard and Seiersen, 2016).
In 2009, the International Standards Organization (ISO), an international non-governmental organization that develops and publishes international standards to harmonize practices between countries, proposed a different definition, which was intended to serve as a reference to promote mutual understanding of and consistency in the use of key risk and risk-related terms (Luko, 2013; Dali and Lajtha, 2012). Specifically, ISO Guide 73 (2009) defined risk as the "effect of uncertainty on objectives" (see 3.1 of ISO Guide 73 (2009)), such as short-term and/or long-term financial goals. In this definition of risk, uncertainty refers to "the state, even partial, of deficiency of information related to, understanding or knowledge of, an event [(i.e., "occurrence or change of a particular set of circumstances," Section 3.3.4.2 of ISO Guide 73)], its consequence [(i.e., "outcome of an event affecting objectives," Section 3.3.5.3 of ISO Guide 73)], or likelihood [(i.e., "chance of something happening, whether defined, measured or determined objectively or subjectively, and described using general terms or mathematically (such as a probability or a frequency over a given time period)," Section 3.3.5.2 notes of ISO Guide 73)]" (see 3.1 notes of ISO Guide 73; for a detailed analysis of risk terminology, see Hoyle, 2018).
Figure 1: Security risk assessment process
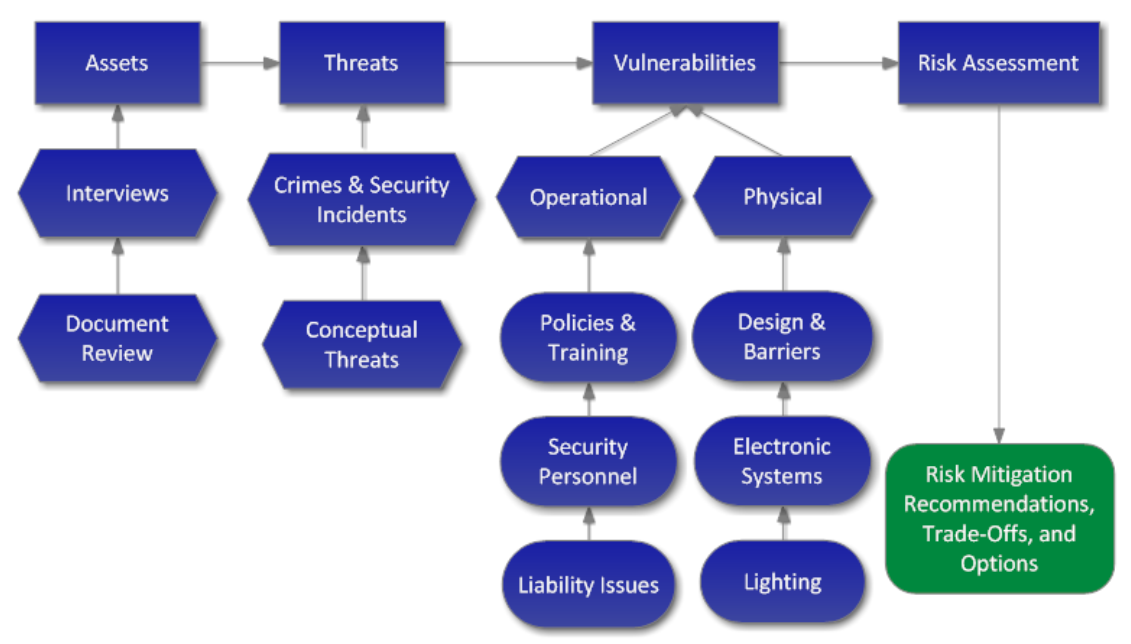
Source: Threat Analysis Group. (2012). Security Risk Management - Methodology.
Risks assessments (depicted in Figure 1) identify vulnerabilities to assets, identify and/or are informed of internal and external threats by the media, public-private partnerships, and/or others in the public and private sectors, and identify impacts and likelihood of threats (NIST, 2018). The purpose of a risk assessment "is to identify … threats; … harm (i.e., adverse impact) that may occur given the potential for threats exploiting vulnerabilities; and … the likelihood that harm will occur" (NIST, 2012; for limitations and challenges of cybersecurity risk assessments and what can be done to overcome these limitations and challenges, see Hubbard and Seiersen, 2016).
After risks are assessed, responses to risks (i.e., risk treatment) are identified and prioritized based on resources (e.g., financial) and needs. Here, measures are implemented to eliminate, reduce or mitigate the risk (Maras, 2014b).
 Next:
Vulnerability disclosure
Next:
Vulnerability disclosure
 Back to top
Back to top