This module is a resource for lecturers
National cybersecurity strategies: Lifecycles, good practices and repositories
The lifecycle of a national cybersecurity strategy includes five phases (ITU, 2018, pp. 16-27):
- The first phase (Phase 1) is the initiation phase, which includes the identification of relevant stakeholders, as well as their roles in the development process, and the creation of a plan for the development of the strategy.
- The second phase (Phase 2), stocktaking and analysis , includes an assessment of the country's cybersecurity posture, the identification of cybersecurity threats, and the evaluation of current and future cybersecurity risks.
- The third phase (Phase 3) is the production of the national cybersecurity strategy . This phase involves drafting the strategy, obtaining feedback from relevant stakeholders, finalizing the strategy based on feedback, and publishing the strategy.
- The fourth phase (Phase 4), implementation , involves the creation of an action plan, determination of which initiatives that are based on the strategy's objectives will be implemented, identification of the resources needed to implement these initiatives, and identification of the specific actions to be taken and the timelines to complete these actions. Metrics and key performance indicators are also specified in this phase to determine the efficiency (i.e., timeliness) and efficacy (i.e., good outcome) of the initiatives.
Overall, action plans include the solutions (or measures) that can be implemented to achieve objectives, the stakeholders responsible for the tasks, the metrics that will be used to determine the timeline for completing the task and whether the desired outcome was achieved. Action plans have been implemented on the national level (e.g., National Security Authority, Action Plan for the Implementation of the Cyber Security Concept of the Slovak Republic for 2015-2020 ) and regional level (e.g., CARICOM's Cyber Security and Cybercrime Action Plan ).
- The fifth phase (Phase 5), monitoring and evaluation , seeks to determine if the action plan is in line with the objectives of the cybersecurity strategy, and evaluates the strategy and action plan to determine if they are up-to-date, meet the cybersecurity needs of the country, and can deal with evolving cybersecurity risks. If the objectives of the cybersecurity strategy are not being met by the action plan, changes are made to the action plan. Changes may also be made to the strategy in the event that it is outdated and/or cannot be applied to new or emerging cybersecurity threats.
Did you know?
Emerging technologies (e.g., blockchain, artificial intelligence, and quantum computing) are mentioned in some national cybersecurity strategies (see, for example, the US National Cyber Strategy and the UK National Cybersecurity Strategy 2016-2021).
Image 2: Lifecycle of a national cybersecurity strategy
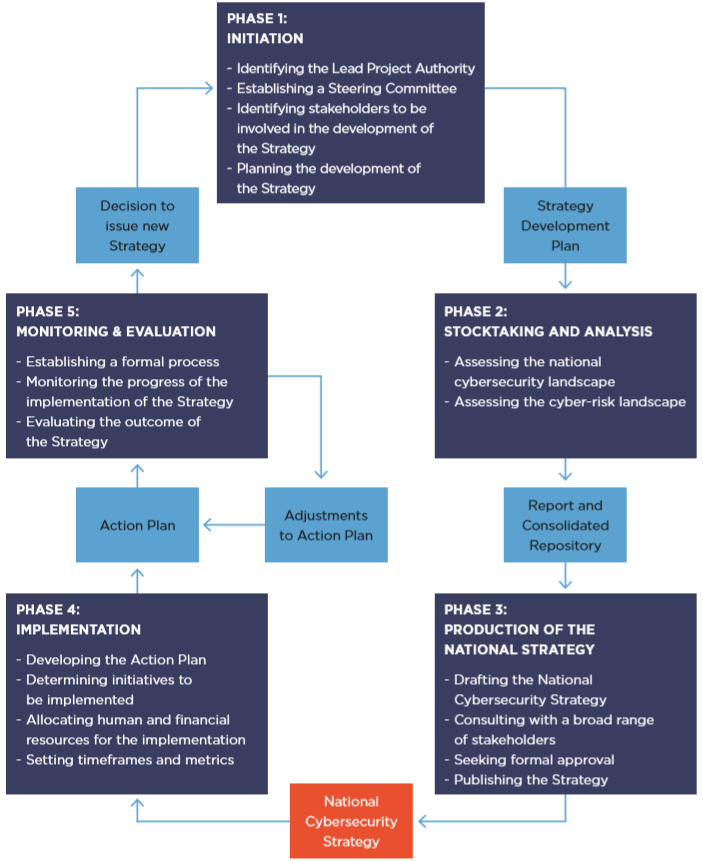
Source: ITU. (2018). A Guide to Developing a National Cybersecurity Strategy , p. 17.
The European Union Agency for Network and Information Security's (ENISA) National Cyber Security Strategy Good Practice Guide (2016) includes examples of strategic objectives and tasks that need to be completed to achieve these objectives and provides guidance on how to develop a national cybersecurity strategy (pp. 14-21). ENISA (2014) also emphasized the need to create evidence-based national cybersecurity strategies by engaging in one-off and periodic assessments of these strategies (i.e., examining outcomes based on predefined evaluation metrics) and utilizing the results of these assessments to modify the strategies and action plans for the implementation of the strategies (pp. 9-10).
National cybersecurity strategies may be included in a single document or parts of the strategy may be disbursed in different instruments that cover some facet of cybersecurity (ITU, n.d.). The International Telecommunication Union (ITU) has a repository of national cybersecurity strategies that includes national policies, plans, and other cybersecurity-related documents (i.e., the National Cybersecurity Strategies repository ). Moreover, the North Atlantic Treaty Organization's (NATO) Cooperative Cyber Defence Centre of Excellence houses NATO and non-NATO member states' cybersecurity strategies and related documents on its website . What is more, ENISA has developed an interactive map that includes the national cybersecurity strategies of European Union Member States and their strategies' objectives (e.g., addressing cybercrime; establishing an incident response capability; engaging in international cooperation; establishing baseline security requirements; and establishing public-private partnerships, to name a few).
 Next:
International cooperation on cybersecurity matters
Next:
International cooperation on cybersecurity matters
 Back to top
Back to top