This module is a resource for lecturers
Formal international cooperation mechanisms
International cooperation depends on harmonized national substantive cybercrime laws, which criminalize cybercrime, and national procedural cybercrime laws that set the rules of evidence and criminal procedure (discussed in Cybercrime Module 3 on Legal Frameworks and Human Rights). International cooperation can also be facilitated by harmonizing, wherever needed, bilateral, regional, and multilateral instruments on cybercrime. Accession to or ratification of regional and multilateral cybercrime instruments is also needed to make these instruments legally binding. For further reading on international cooperation to combat transnational organized crime in general, see also the University Module Series on Organized Crime (particularly Module 11 on International Cooperation to Combat Transnational Organized Crime)
International cooperation is facilitated by bilateral, regional, and multilateral cybercrime treaties (discussed in Cybercrime Module 3 on Legal Frameworks and Human Rights) as long as dual criminality exists (i.e., a clause in treaties requiring the alleged conduct to be considered illegal in cooperating countries). Without dual criminality and harmonized laws, cybercrime safe havens are created whereby perpetrators of cybercrime cannot be prosecuted. This was observed in the now infamous 2000 Love Bug virus case, whose creator and distributor could not be prosecuted because his acts were not considered a crime in his country (the Philippines) at the time of the incident.
Nonetheless, international cooperation may still be possible even without a strict interpretation of the dual criminality requirement. What is more, "whenever dual criminality is considered a requirement, it shall be deemed fulfilled irrespective of whether the laws of the requested State Party place the offence within the same category of offence or denominate the offence by the same terminology as the requesting State Party, if the conduct underlying the offence for which assistance is sought is a criminal offence under the laws of both States Parties" (Article 43(2), UN Convention against Corruption of 2003).
There are, however, exceptions to the dual criminality requirement. For instance, Article 29 (3) of the Council of Europe's Convention on Cybercrime of 2001 does not require dual criminality for the "expedited preservation of stored computer data" "by means of a computer system, located within the territory of that other Party and in respect of which the requesting Party intends to submit a request for mutual assistance for the search or similar access, seizure or similar securing, or disclosure of the data" for the substantive offences included in this Convention (Articles 2 through 11). Article 29(4) provides a right of states to refuse preservation requests if they require dual criminality for mutual assistance for offences other than those included in the Convention.
In addition to dual criminality, another substantive requirement for international cooperation is respect for international human rights obligations (UNODC, 2013, p. 205). Requests for international cooperation can be denied if the request will result in the responding state violating its international human rights obligations by responding to the request.
Did you know?
The UNODC Cybercrime Repository has a " Lessons Learned" feature covering topics relating to prevention; investigation (investigative powers, obtaining data from service providers, and other investigative measures); evidence and procedure (court practice, digital evidence, jurisdiction, and other procedural practice); international cooperation (expedited cooperation, extradition, international cooperation, and mutual legal assistance); technical assistance; and prosecution. The repository can be searched by topic or country.
Formal mechanisms for international cooperation include bilateral, regional, and multilateral cybercrime treaties. Indeed, cooperation factors prominently in these treaties. For instance, the Commonwealth of Independent States' Agreement on Cooperation in Combating Offences related to Computer Information of 2001, includes several articles dedicated to international cooperation (Articles 5-7), covering the types of cooperation covered in this Agreement (i.e., information exchange; provision of legal assistance pursuant to international instruments; and cybercrime prevention, detection, suppression and investigation of cybercrime; to name a few), as well as the manner in which Member States can request assistance, and the guidelines for Member States on how to execute these requests. Article 8 of this Agreement includes the circumstances under which a request for assistance can be refused (i.e., when this request violates a state's national law) and the requirement of the refusing state to notify the requesting state in writing that the request was refused and the reason(s) for refusal.
Did you know?
The Ibero-American Cooperation Agreement on Research, Assurance and Evidence on Cybercrime Issues ( Convenio Iberoamericano de Cooperación sobre Investigación, Aseguramiento y Obtención de Prueba en materia de Ciberdelincuencia) also seeks to promote cooperation between signatories with regards to evidence collection and preservation in cybercrime cases.
Furthermore, Articles 32 and 34 of the League of Arab States' Arab Convention on Combating Information Technology Offences of 2010 include provisions on mutual assistance, procedures for cooperation, and mutual assistance requests. What is more, in the African Union Convention on Cyber Security and Personal Data Protection of 2014, Article 28 includes provisions on harmonization, mutual legal assistance on cybercrime matters, and information exchange. The latter provision calls on states to establish institutions that can facilitate the exchange of information about cybersecurity threats and vulnerabilities, such as Computer Emergency Response Teams (CERTs) or Computer Security Incident Response Teams (CSIRTs) (discussed in Cybercrime Module 9 on Cybersecurity and Cybercrime Prevention: Practical Applications and Measures). Under Article 28(4) states are instructed to "make use of existing means for international cooperation," which can include "international, intergovernmental, regional or… public private partnerships," to respond to cybercrime.
Other mechanisms that facilitate international cooperation in the investigation and prosecution of cybercriminals are mutual legal assistance and extradition treaties. Mutual legal assistance treaties (MLATs) are agreements between countries that apply to a list of crimes and delineate the type of assistance provided by each country (e.g., evidence) in investigations (Maras, 2016, p. 78) (see Module 11 on International Cooperation to Combat Transnational Organized Crime of the University Module Series on Organized Crime for more information on mutual legal assistance). The list approach is quite outdated and does not account for the evolving nature of cybercrime. Understanding the changing nature of crime (and cybercrime), in some MLATs, instead of lists of crimes, parties agree to cooperate in investigations and prosecutions of all offences proscribed under their respective national laws (with a few exceptions) (Garcia and Doyle, 2010). Requests for mutual assistance (see Figure 1, which depicts an MLAT request between an EU country and a non-EU country) must be in writing and include information about: the requesting authority; the purpose of the request; the description of the request; the investigation or court proceedings to which the request for assistance pertains; the description of the offence or offences and laws violated; any requests with regards to the procedures to be followed to obtain, preserve, and ultimately transfer physical and digital evidence (discussed in Cybercrime Module 4 on Introduction to Digital Forensics) to the requesting authority; time limits for data preservation requests and for executing these requests; and any other information that would assist the state receiving the request in executing the request (see, for example, Article 5 of the Economic Community of West African States or ECOWAS Convention on Mutual Assistance in Criminal Matters of 1992).
Figure 1
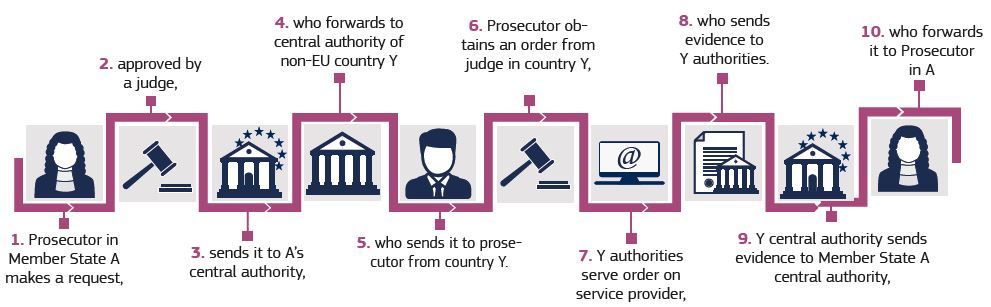
Source: European Commission. (2018). Security Union: Facilitating Access to Electronic Evidence.
Requests for mutual assistance may be refused in certain circumstances. For instance, if the request "would prejudice its sovereignty, security and public order" (Article 4 of ECOWAS Convention on Mutual Assistance in Criminal Matters; see also Article 2 of the European Convention on Mutual Assistance in Criminal Matters of 1959, Article 25(4) of the Council of Europe's Convention on Cybercrime, and Article 18 of Algeria's Law No. 09-04 of 14 Sha'ban 1430 Corresponding to 5 August 2009 Containing Specific Rules on the Prevention and Fight Against Information Technologies and Communications Crimes). Mutual legal assistance requests can be denied if, for example, requests "concern… an offence[s] which the requested Party considers …political offence[s] or …offence[s] connected with… political offence[s]" (Article 25(4) of the Convention on Cybercrime). Requests for data can also be denied if the assistance or disclosure sought would result in the responding state's violations of international human rights obligations (UNODC, 2013, p. 204) (discussed in Cybercrime Module 3 on Legal Frameworks and Human Rights).
Some states (e.g., Brazil, Japan, and Ukraine) provide mutual legal assistance if reciprocity is guaranteed (i.e., if a request of the same kind by the responding state is honoured by the requesting state in the future). What is more, the Council of Europe's Convention on Cybercrime of 2001, acts as an MLAT for countries that do not have one with the country requesting assistance. In the absence of treaties and agreements, letters rogatory (i.e., written requests from national courts that include "information about the case, description of the evidence needed and why it is needed, and a promise of reciprocity in future cases"; Maras, 2016, 78-79; Bell, 2007) can also be used to obtain assistance on cybercrime matters (see Module 11 on International Cooperation to Combat Transnational Organized Crime of the University Module Series on Organized Crime for more information about letters rogatory).
Significant time delays (i.e., "timescale of months") are also experienced with other formal cooperation mechanisms (i.e., mutual legal assistance and extradition) (UNODC, 2013, p. 207; Module 11 on International Cooperation to Combat Transnational Organized Crime of the University Module Series on Organized Crime). These time delays are particularly problematic due to the volatility of digital evidence (see Cybercrime Module 4 on Introduction to Digital Forensics).
Drafting mutual legal assistance requests
While certain countries include guidelines for mutual legal assistance requests and letters rogatory, and even provide exemplars, this practice is not universal. To assist countries in drafting requests for mutual assistance, the United Nations Office on Drugs and Crime (UNODC) created a Mutual Legal Assistance Request Writer Tool in an effort to streamline the process by harmonizing formats for requests, and in so doing, facilitating the swift submission and response to these requests for assistance.
Extradition treaties, such as the European Convention on Extradition of 1957 and the OAS Inter-American Convention on Extradition of 1981, are agreements to arrest and/or extradite individuals to the requesting country if punishment thresholds are met for extraditable offences (see Module 11 on International Cooperation to Combat Transnational Organized Crime of the University Module Series on Organized Crime for more information on extradition treaties). For example, Article 3 of the ECOWAS Convention on Extradition of 1994 lists the punishment threshold at a "minimum period of two years." Regional arrest warrants, such as the European Arrest Warrant, enable the arrest of offenders for computer-related crimes "punishable in the issuing Member State by a custodial sentence or a detention order for a maximum period of at least three years…without verification of the double criminality [or dual criminality] of the act" (Article 2(2), Council Framework Decision 2002/584/JHA of 13 June 2002 on the European arrest warrant and the surrender procedures between Member States).
The existence of an extradition treaty does not guarantee that a person will be extradited to the requesting country. This was observed in the case of Lauri Love, a British hacker, whose extradition to the United States was denied (Parkin, 2017), despite the existence of the UK-US Extradition Treaty of 2003.
Moreover, extradition treaties include conditions under which extradition will not be granted. For example, the OAS Inter-American Convention on Extradition denies extradition requests when the punishment for the offence is life imprisonment or the death penalty (Article 9). Extradition is also denied in cases where the person to be extradited will be subjected to inhuman or degrading treatment or punishment (e.g., Article 5 ECOWAS Convention on Extradition and Article 9 OAS Inter-American Convention on Extradition). Extradition requests may be further denied for other reasons, such as a lack of sufficient evidence to justify extradition (e.g., Botswana Extradition Act of 1990), when the request involves a non-extraditable offence (e.g., a military offence, Article 7 of the ECOWAS Convention on Extradition), or when the subject of the extradition request is a national of the country receiving the request (e.g., Article 698 of the Algerian Code of Criminal Procedure and Article 5 (LI) of the Brazilian Constitution). With respect to the latter, the principle of non-extradition of nationals is enshrined in the constitution and regional and international instruments. Irrespective of this principle, "public international law dictates that States have the legal obligation to either extradite or prosecute ( aut dedere aut judicare) persons who commit serious international crimes" ( Module 11 on International Cooperation to Combat Transnational Organized Crime of the University Module Series on Organized Crime). Some arrest warrant treaties may also exclude specific offences, such as certain political offences (e.g., see Article 3 of the Caribbean Community or CARICOM Arrest Warrant Treaty of 2008).
 Next:
Informal international cooperation mechanisms
Next:
Informal international cooperation mechanisms
 Back to top
Back to top